Powerful security that's simple to use
SendSafely is so easy to use, you won't even notice the sophisticated security at work behind the scenes.
Here's a quick look at how Bob would securely send items to Alice using SendSafely.
For a more technical overview of how SendSafely works, refer to our Security Overview page.

Bob creates an encryption key that will be used to protect the files he wants to send to Alice. The files are encrypted using that key before they are uploaded to SendSafely.
- The key consists of a Client Secret and a Server Secret
- SendSafely generates the Server Secret
- Bob's PC automatically generates the Client Secret
- SendSafely provides Bob with a link that he can send to Alice in order to access the files
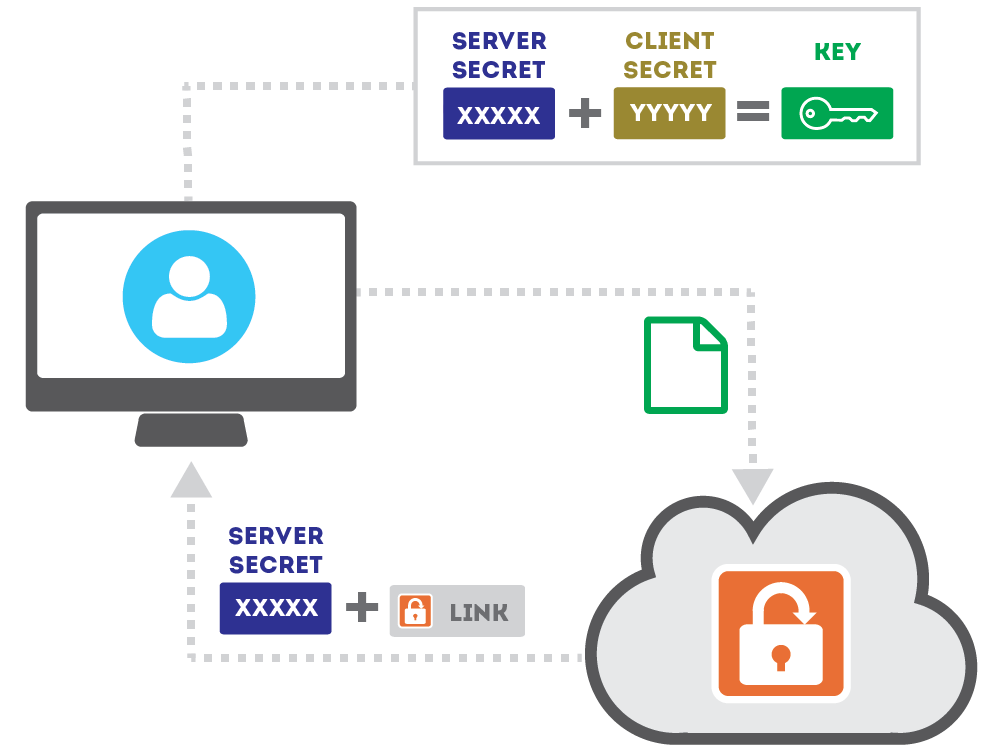
Bob sends Alice a secure link to SendSafely that also includes the Client Secret. The secret is embedded within the URL Anchor of the link, so that it won't be disclosed to the server when the link is clicked.
SendSafely will verify Alice's identity before allowing access to the files.
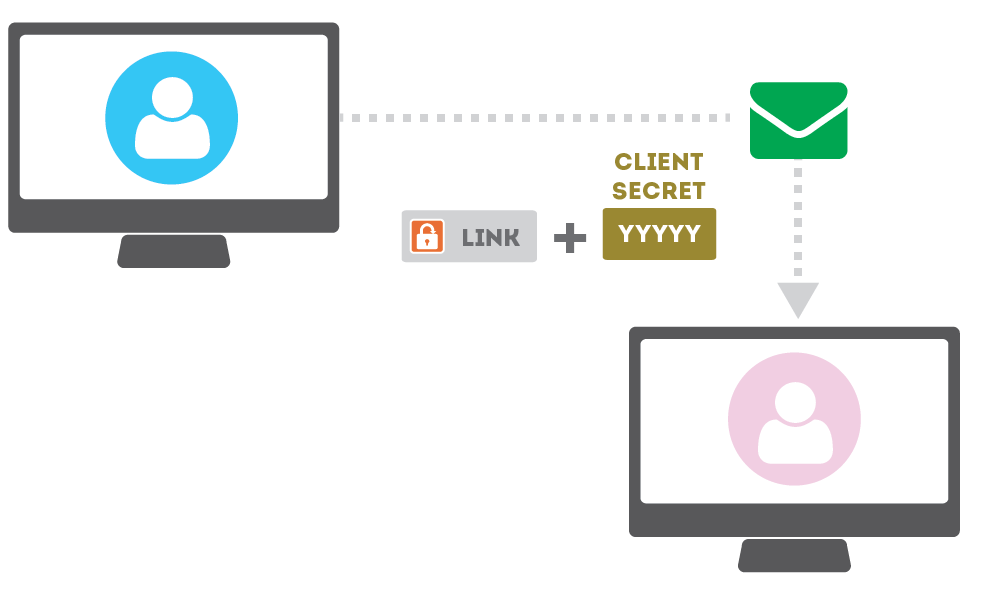
When Alice follows the link, her identity is verified by SendSafely using a one-time pass code to her email or phone.
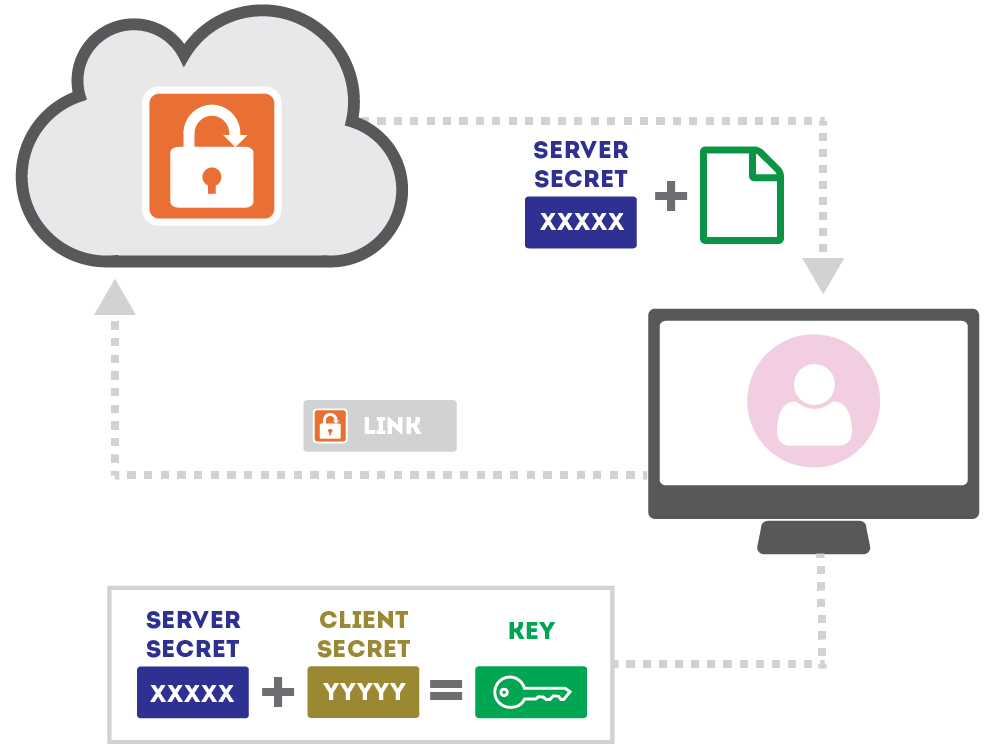
Once she is verified, the Server Secret and encrypted file is provided to her browser.
Alice's browser is able to re-compute the full key using the Server Secret and the Client Secret (read from the URL anchor) and decrypts the file.
Send files to anyone
You can send anything to anyone using SendSafely. There's nothing to install, and the people you share with don't need to register with us. We've made it as simple as possible...if you can use a web browser, you can use SendSafely.
Request files from other people
We give each user their own personal URL that anyone can use to send them items securely, even if they don't have a SendSafely account. Any time you send something with SendSafely, your recipients can also reply back to you.
Total confidentiality and privacy
Services like Dropbox only encrypt your files in transit. Once uploaded, they have full access to all of your information. With SendSafely, nobody can see your data other than the people you give access to...not even us.
Security you can rely on
With SendSafely, your information is encrypted before it ever leaves your machine. We use OpenPGP encryption with AES-256, widely recognized as one of the most reliable and proven encryption protocols available today.




